Hi! I'm Jarred, a recent cybersecurity graduate with a passion for offensive security, penetration testing, and digital forensics. With hands-on experience in both government and private sector environments, I specialize in identifying vulnerabilities and developing comprehensive security solutions.
Having just completed my master's degree on full scholarship at NYU, I bring both academic rigor and real-world experience to every project for innovative problem-solving. My background spans from NASA research to penetration testing at financial institutions.

M.S., Cybersecurity
B.S., Computer Science & B.S., Cybersecurity
Security Tools
Programming
Security Analyst
- Achieved 25% increase in efficiency of setup process by parallelizing backend operations in 14 code dependencies for data fetching and streamlining logging output verbosity for government law repositories.
- Expanded system compatibility by 30% by enhancing hardware security of two-factor authentication protocols.
- Impacted UX for 40k+ users across high-traffic open-source repositories by resolving 6 critical GitHub issues, boosting repository health and reducing delays and bug-related downtime during edits to repositories.
Information Systems Specialist
- Reduced costs by ~$150k by designing and implementing in-house resume construction system using ASP.NET, C#, HTML5, and SQL to eliminate need for Microsoft Office 365 licenses at 18 career centers statewide.
- Spearheaded comprehensive user support and training documentation process to optimize future employee onboarding and decrease time spent on future software development and feature addition efforts.
- Boosted interdepartmental productivity by engineering and launching a DevOps-compatible project management system complemented by system entity mapping diagrams and dashboards for review by upper management.
- Decreased setup errors by 40% and accelerated new-hire readiness by streamlining user-account turnaround in Salesforce CRM; implemented standardized provisioning processes according to COVID remote work policy.
- Strengthened agency cybersecurity posture by reviewing and correlating Nessus scan results to known CVEs for remediation, reviewing NIST and MITRE ATT&CK frameworks for compliance with federal guidelines and risk objectives, and supporting hardware/system implementations with technical teams.
Penetration Testing Engineer
- Achieved a reduction in successful phishing attempts by 58% by executing cybersecurity-focused company-wide newsletter campaign on email phishing, password security, and social engineering tactics, impacting 1k+ employees.
- Enhanced enterprise threat detection and network security by configuring and deploying honeypots using Raspberry Pi.
- Performed comprehensive network penetration testing and verified patching of previously discovered vulnerabilities by exploiting web applications and scanning network traffic logs using Metasploit, Wireshark, Maltego, and Shodan.
PSL Research Test Engineer
- Saved ~$1M in costs per test run by developing a virtual simular in IEC Structured Text language that enabled the simulator to emulate the addition of fuel into the propulsion sy stems laboratory with NASA mechanical test engineers.
- Increased projection accuracy by 80% by analyzing existing propulsion data with Excel for accurate trend projections; ensured precise replication of in-flight environments for propulsion emulation through collaboration with engineers to simulate conditions and facilitate accurate readings comparable to airborne flights at high altitudes.
- Authored paper detailing the processes, calculations, scalability, and results of the completed simulator addition.
Offsec CTF Challenges
- Analyzed malicious artifacts and reverse engineered 20+ malware samples using Ghidra and Binary Ninja to identify actor TTPs and attack chains.
- Exploited 20+ vulnerabilities across buffer overflows, register corruption, and glibc/heap memory issues by completing 4 weekly CTF challenges for 14 weeks using reverse engineering tools to analyze C executables, identify vulnerabilities, and develop Python Pwntools scripts for vulnerability exploitation and administrator access.
- Achieved root access on 5 servers by leveraging HTML encoding and SQL-based exploits for web challenges, documenting vulnerabilities and binary analysis findings, exploitation techniques, and payloads in extreme detail.
SQL Database Modeling and Querying
- Designed and executed complex SQL queries for threat hunting across 5,000+ data records, enabling rapid identification of anomalous patterns and indicators of compromise.
- Enabled real-time inventory lookup of over 5k+ items by designing normalized relational schemas from ER diagrams and writing/executing complex CREATE TABLE, INSERT, SELECT, and JOIN statements using MySQL to simulate a donation system for furniture items.
- Validated the design of 3 schemas and database performance by simulating full-stack backend logic using MySQL and Flask for interactive website development.
Web, Mobile, Container, and Binary App Security
- Web App Security Assessment: Identified and remediated 4 critical vulnerabilities (XSS, CSRF, SQL Injection, command injection) in Django web application; implemented comprehensive security fixes and automated regression testing via GitHub Actions.
- Mobile App Security: Conducted security audit of Android gift card application, fixing Intent vulnerabilities, implementing HTTPS encryption for REST API communications, and removing privacy-invasive monitoring code.
- Container & Kubernetes Security: Secured containerized application deployment by implementing Kubernetes Sealed Secrets for credential management, configured Prometheus monitoring with custom security metrics, and established CI/CD pipeline with automated security testing.
- Binary Security & Fuzzing: Identified and fixed 6 buffer overflow and memory corruption vulnerabilities, achieving an 85%+ code coverage through systematic case development by performing a vulnerability assessment on legacy C application using AFL++ fuzzer and coverage analysis.
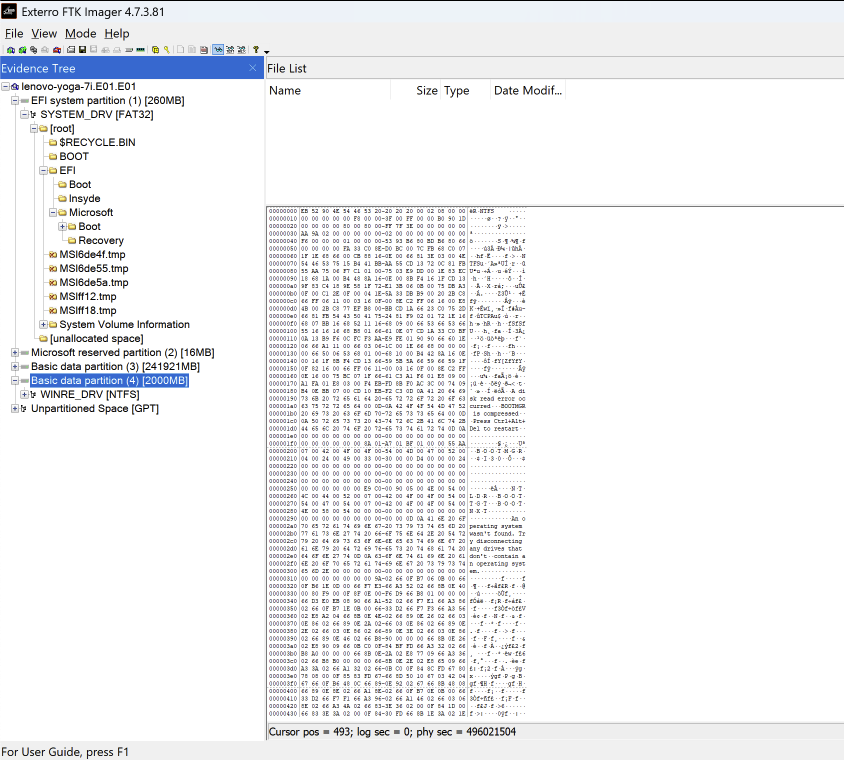
Obfuscated Evidence Recovery
- Conducted threat intelligence analysis by reassembling deleted evidence from 8 system images and correlating findings to identify attack patterns and TTPs.
- Reassembled deleted and obfuscated evidence from 8 system images using Scalpel and FTK Imager for recovery of hashes, user accounts, logs, documents, and metadata to deepen digital evidence recovery insights.
- Identified 80+ functions, libraries, and security vulnerabilities by reverse engineering unknown executables, creating and inspecting forensic images/file systems with Procmon and Pestudio.
Network Penetration Test for NBN Corporation
- Achieved root access on 2 servers by identifying critical XSS, SQL injection, and local file inclusion vulnerabilities in a penetration test for NBN Corporation, assessing risks using NIST CVSS Version 3 with average score of 8.86.
- Recommended 5 immediate security fixes and mitigations (input sanitization, system updates, enhanced password policies, microservice architecture implementation) to isolate assets and prevent unauthorized server access.
Cyberassess: Cybersecurity Competency Assessment
- Designed and developed 75% of the interactive assessment modules in Articulate 360 while acting as primary liaison between the team and professor, implanting proactive deadline strategies for delay prevention.
- Spearheaded the design and delivery of 4 final project materials and accompanying presentation to an audience of over 60 colleagues, faculty members, and guests from other projects and the surrounding community.
- Informed 10+ team and faculty members of individual task progress, status, and projected completion times by compiling and distributing 15 comprehensive weekly reports.
For creative inspiration, cybersecurity professionals should look beyond their screens. Whether it's exploring new attack vectors, practicing with different tools, or diving into the latest research papers, the experiences we have outside of traditional security work often fuel our most innovative defensive solutions. Balance isn't just about productivity—it's about perspective.